OpenSSH server config hardended using https://www.sshaudit.com/
Posted on za 25 december 2021 in servers
Yesterday I received a short mail from Mischa running OpenBSD.Amsterdam that he had hardened the sshd configuration for the OpenBSD.Amsterdam servers based on test results from the site sshaudit.com
Most of my OpenSSH servers are behind restrictive allow lists, but my OpenBSD VM at OpenBSD.Amsterdam is not as restricted, so I decided that I could have it checked.
OK, there was room for improvement, scoring a F :-(
So I fiddled some with communication parameters on a local Ubuntu and OpenBSD VM I have, validating that I could still properly access it after any of my changes. When the changes seemed to work OK, I deployed them to systeemkabouter.nl and reran the test at sshaudit.com.
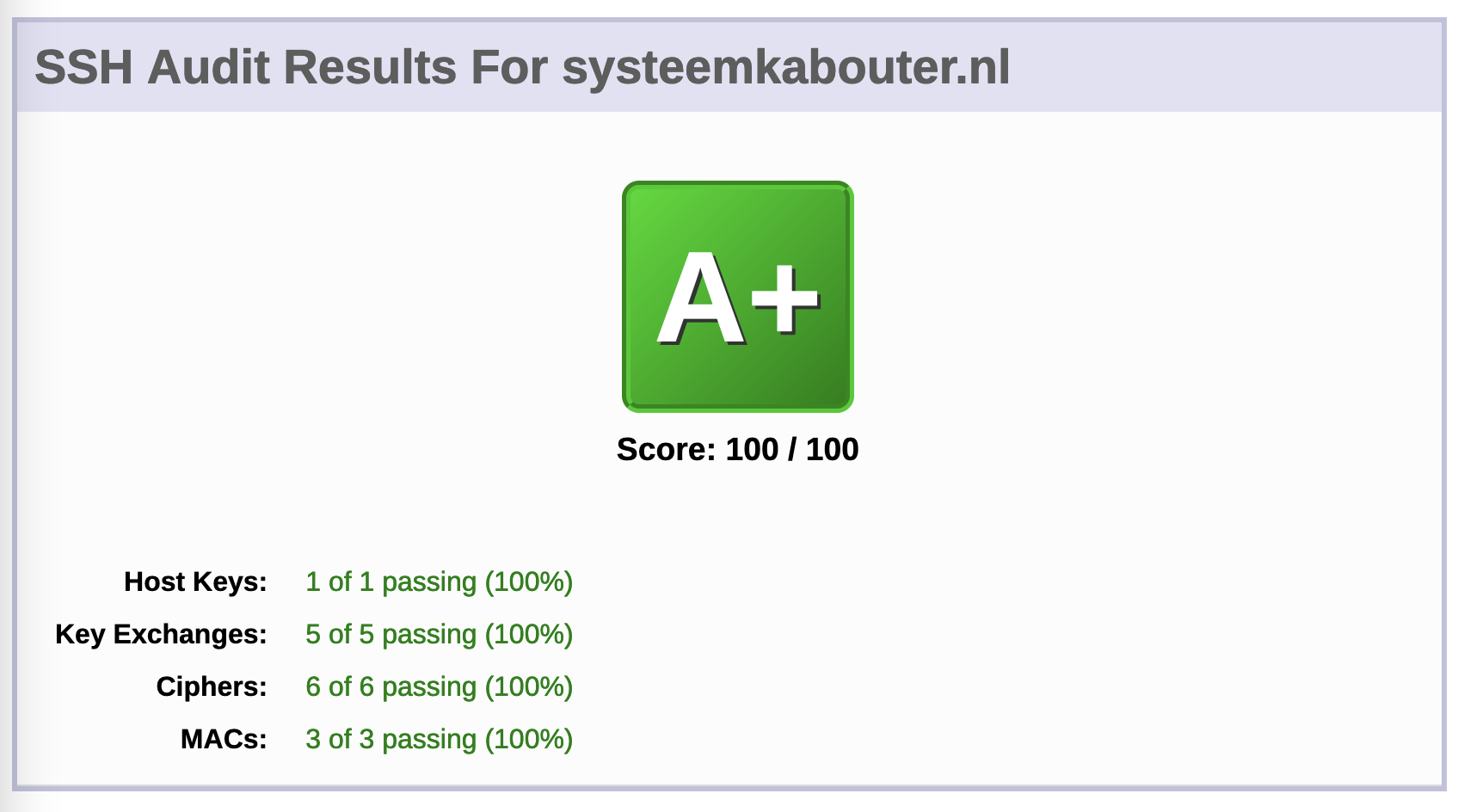
I think it took 2-3 rounds of changing, testing and deploying things, but than I was able to produce an A+ on sshaudit.com. Nice!
In the end I changed/added the following lines to all my sshd configs:
HostKeyAlgorithms ssh-ed25519-cert-v01@openssh.com,ssh-ed25519
KexAlgorithms -diffie-hellman-group1-sha1,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com
These settings should work fine on modern OpenSSH servers, but as always: test before deploying to remote hosts. These settings work for me on OpenBSD 7, Ubuntu 20.04 and Debian 10.
By changing the host key type used, I did run into a round of host key changed errors/warnings. So you might want to prepare for that. Or set up public keys in DNS ;)
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ED25519 key sent by the remote host is
SHA256:fGvR97Gb+ImQuydFJN/WNauh8kBnVZOfOEs6bZgEfjk.
Please contact your system administrator.
Add correct host key in ~/.ssh/known_hosts to get rid of this message.
Offending ECDSA key in ~/.ssh/known_hosts:28
Note to self: rerun sshd checks in a year or so.