Homelab egress
Posted on za 16 juli 2022 in homelab
Part of rebuilding my home lab is putting prober Internet filtering in place. The gateway for my home lab is a APU2 running OpnSense. After some initial bootstrapping, I changed the firewall rules in such a way that http/https traffic is only allowed from a particular host, the vm running http proxy software.
All other hosts must either tunnel their traffic via the tor service on my OpnSense router or run traffic through the designated egress/outgoing proxy running on an OpenBSD VM.
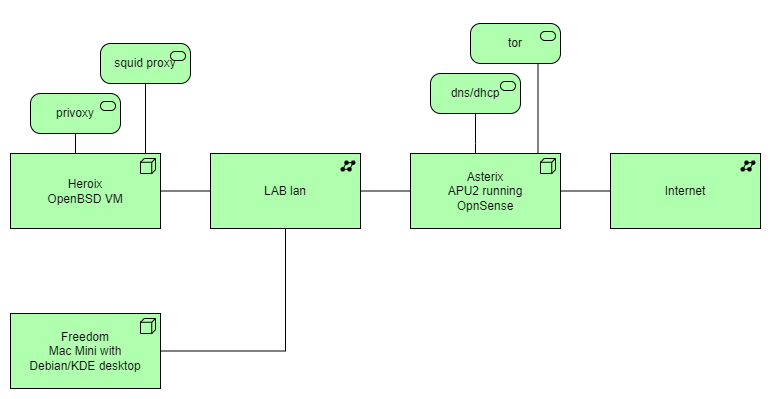
This OpenBSD VM is running squid proxy, which is configured to use a privoxy instance as its default parent. The privoxy instance in turn runs all traffic through the tor service on the OpnSense router
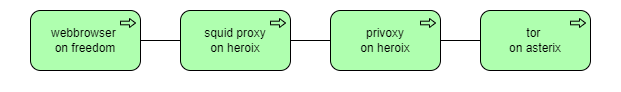
This breaks things. Some Internet sites just block tor users. Others put up extra security checks to allow access. Still others just fail for some none apparent reason.
So this is just an experiment to see how many of my daily sites break. And when it breaks, I configure the squid proxy to connect to these sites directly instead of channeling traffic through tor
So far I only had to put two sites/domains on the exclusion list. But more will follow over time I guess. But for most part the sites I rely on seem tor friendly. And while running your requests over tor could be very slow in the past, sites load rather quick and painless at this time. So the trade-off seems a lot smaller nowadays.
Relevant config part of squid
Below you can see a list of domains being defined that will not be contacted via tor. All undefined traffic will.
acl not-via-tor dstdomain .example.com
acl not-via-tor dstdomain .torblockingsite.tld
# privoxy parent
cache_peer 10.10.10.14 parent 8118 0 no-query default
cache_peer_domain 10.10.10.14 !not-via-tor
never_direct deny not-via-tor
never_direct allow all